Build.

Secure.

Optimize.

All with the press of the Easy Button.
Of course, we don't mean that literally. This is DevSecOps.
It's considerably more difficult than that on our end.
Alright. You know it's metaphoric now. Go on. Press it. It's right there.
There’s an ideal DevSecOps stack waiting for you. We can build it. We can help you secure it. We can help you optimize it. We have the technology. (And the people). (And the processes). That's why they call us the Secure Kubernetes Easy Button.
The SK8EB for short.












Hi. 👋 We’re Infinite Ranges. We're the Super-Nerds' Super-Nerds.
As you might be able to tell, we like to call ourselves “The Secure Kubernetes Easy Button.” (The SK8EB).
But you’re probably already saying to yourself: "Yeah alright, what is that, exactly? I don't just go pushing buttons willy-nilly."
We like that. You're a straight-shooter. And for that very reason...
We'll humor your incredulity
with a fun metaphor.
Think of DevOps as the renowned gambler, rogue, and dentist Doc Holliday.
Cybersecurity, well of course that’s his lawman friend, Wyatt Earp. Both are pretty cool in their own right, right? But here's the deal: You really shouldn’t have one without the other.
We’re basically those guys combined. 😎
Instead of a cool cowboy name (which are all taken), we call ourselves “The Secure Kubernetes Easy Button." Also, not an unshocking amount of people have yet to see Tombstone.
Anyway, by mastering Kubernetes we’ve been able to perfect the trio of security, orchestration, and timing. We've also found a way to find people who can help.
And just like those two dudes who Kurt Russell and Val Kilmer played so masterfully... we're really good at our jobs.
You’re probably wondering by now: "Yeah yeah. What about the button?" Yes, it's still up there, by the way.
We have a backup secret, thought-activated button. And that button has been activated.
We don’t mean to startle you... but this means you’ve notified a hyper-specialized Navy Seal-esque team of Super Nerds who has mastered everybody’s favorite open-source container orchestration system, AND the art of cybersec incident response.
Basically, the button is connected to a little bell that rings in their office. They’re all on high alert now. They’re ready to engage.
I’m scared, you’re saying. That’s a lot of pressure.
Don’t be frightened. (It's just a button to our contact page).
What we're basically saying is that we’re dangerous in three ways, all of them are the good kind of dangerous.
- BUILD: We send legacy companies to the cloud, and we do so securely (legacy is just another word for “ready to be exploited”).
- SECURE: We help companies respond to cybersecurity incidents in record time; and we pen-test/redteam with the best of them.
- OPTIMIZE: We help Cloud and ISV companies make good on their promises to their customers — in all the ways.
Simply put: we’ve got your back. We’ll be your Huckleberry.
In four ways, in fact.
1. We teach.
We help customers understand the tools, services, and tech personas needed in this digital-first IT world.
2. We do.
We serve as certified install and implementation experts with 35+ partners, all driven by customer business outcomes.
3. We improve.
We speed up adoption for ISV and Cloud partners by pairing their services with the right SMEs.
4. We staff.
We provide talent and help our customers build teams that will be overseeing their new environment.
Consult the graphic!
It's where we Super-Nerds are Super-Nerdiest. Plus, we got to make a cool symbol.
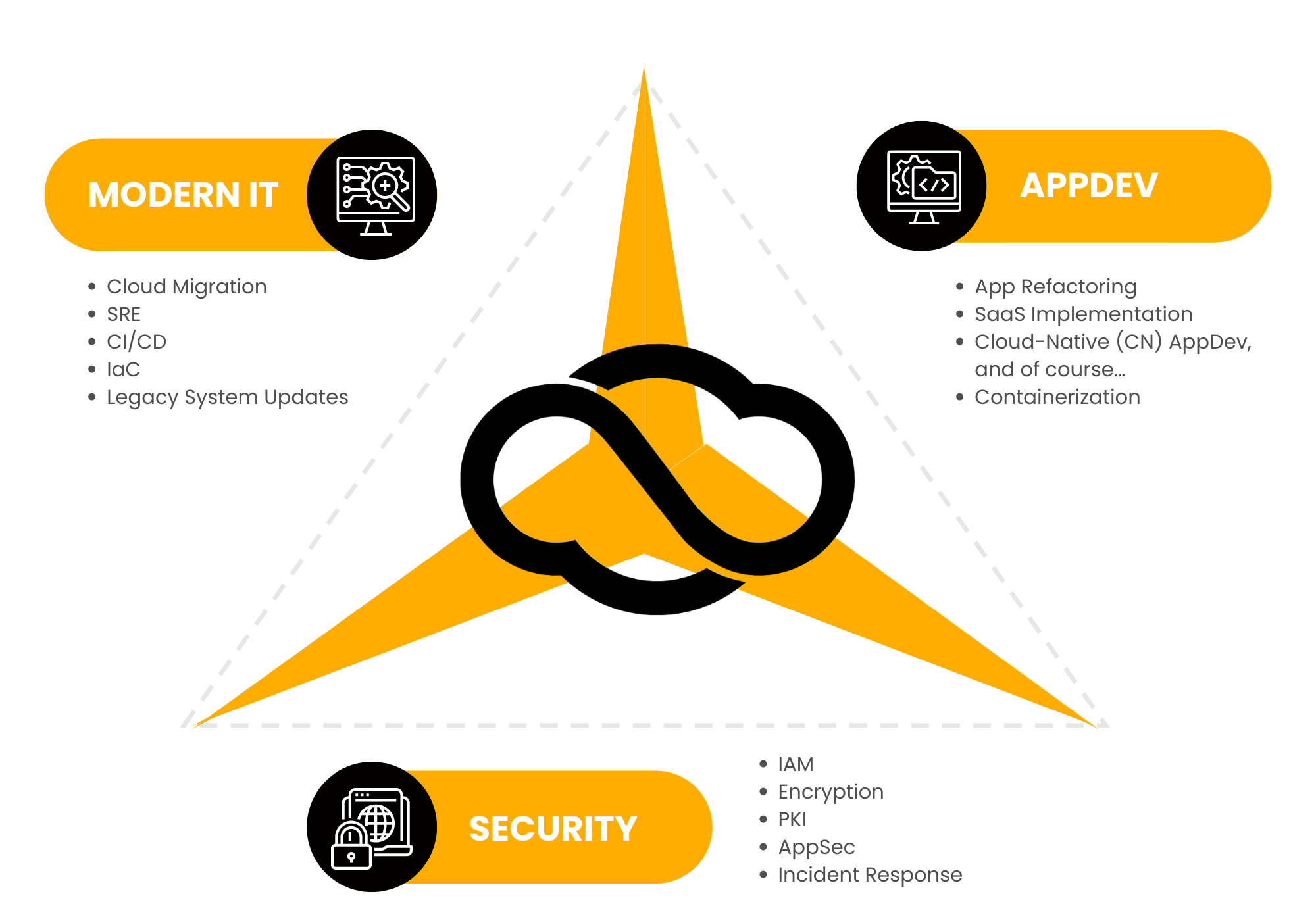
So yeah. While there are clearly a bajillion ways to refactor apps, stiffen your security posture, or to entirely rethink your company’s DevOps/DevSecOps mindset, we know there’s only one way to do it right: By focusing on your very specific best-case-scenario outcomes.
That’s it.
Oh and here’s another graphic for good measure:
And it all boils down to this:
You can’t have the right outcome without the right products, people, or most importantly processes.
Our process-oriented solutions in Encryption, Infrastructure as Code, and Identity Access Management are essential to ensuring the success of a customer’s implementation of a product. Our Super Nerds have built careers over many years in this space — we call them the Forefathers of Kubernetes — (not to their faces, though) and as such, they also know how to separate the wheat from the chaff. Speaking of which… we’d be remiss not to show off about our shiny toy:
The RangeX Platform
To help our Super Nerds help you scale, we built this proprietary recruiting automation engine that can find the right talent for an outcome within three to five business days (AKA at lightspeed, compared to other platforms).
So if the alacrity of moving to the cloud, or finally dealing with that shelfware, is an issue for you (or your clients or your clients’ clients), let us know about that HERE. We’d be glad to help. And also, to tell these Super Nerds to stand down.
So in conclusion:
We’re the consummate experts in this space. No big deal. And not just that, we’re easy to work with, and can make downright difficult concepts easy to understand. Sounds like the Secure Kubernetes Easy Button — The SK8EB — to you?
We sure hope so.
So now. Press away.

